Use GPG, an open-source encryption standard, to ensure data you are transmitting is secure

The easiest way by far to share sensitive information is to use a commercial off-the-shelf password manager. Here at Forward Force, we use LastPass, but there are countless other good options. However, sometimes password managers create obstacles that people are not always willing to deal with. One of those obstacles would be creating and verifying an account with a service that people are going to use once; encrypting the message that is to be transmitted is an alternative to password managers or other commercial products that can accomplish that.
What is PGP
PGP (Pretty Good Privacy) is a data encryption and decryption program that provides cryptographic privacy and authentication for data communication. One of the features of PGP is the ability to encrypt a file using someone else’s public key, which allows them to decrypt the file using their private key. GPG is an open-source encryption standard, while PGP is a proprietary solution owned by Symantec.
Here is an example of how you might use PGP to encrypt a file using a public key:
Installation, setup, and usage
- Download and install a PGP program, such as GnuPG (also known as GPG). This will give you access to the command-line tools you need to encrypt and decrypt files.
- Obtain the public key of the person you want to encrypt the file for. This can usually be done by asking the person for their key or by searching for their key on a public key server.
- Once you have the public key, you can use the
gpgcommand-line tool to encrypt the file. The basic syntax for encrypting a file is as follows:
gpg --encrypt --sign --recipient [email address or key ID] [file to encrypt]
For example:
gpg --encrypt --sign --recipient teodor@forward-force.com file.md
To install GPG on a Mac, you can simply use Howmebrew like so:
brew install gpgOnce gpg is installed, you will need to create your public and private key-pair, which which as simple as:
gpg --gen-keyGPG will ask you a series of questions; answer them as best as possible, and make sure you secure your key with a password. As a best practice, you should back up your private key to a secure location, such as a USB drive or an online storage service. In addition, it would be best to note your key’s ID and passphrase, as you will need them to use your key in the future.
There is an app for that
You can make your life even easier by downloading an app that can handle all of the above for you, allow you to encrypt and decrypt files and register your key with the Key Server; you can download the GPG keychain from here.
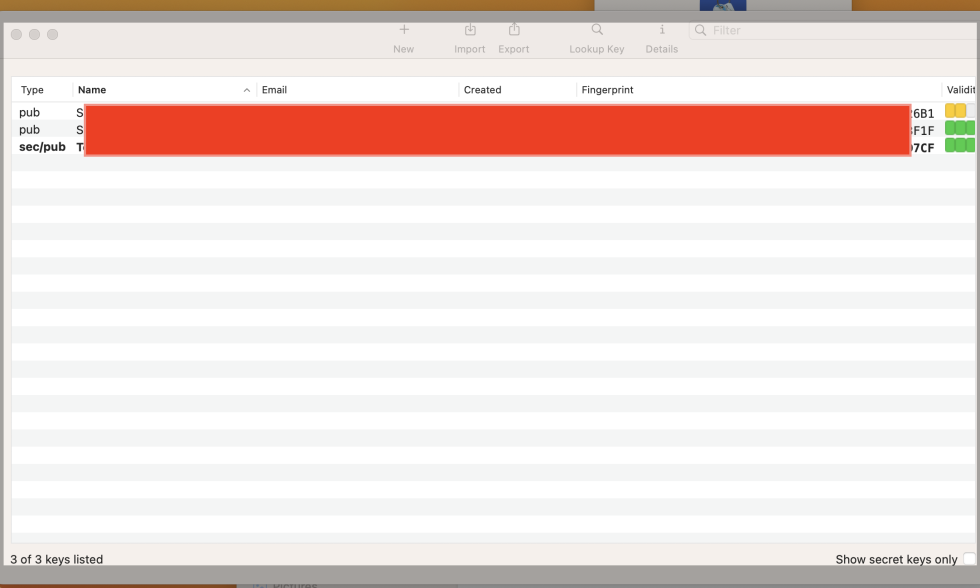
GPG Keychain will manage your keys, auto-discover them, and provide other useful utilities. To encrypt to decrypt a file using GPG Keychain, simply select the file, right click, and choose your operation from the context menu like shown below:
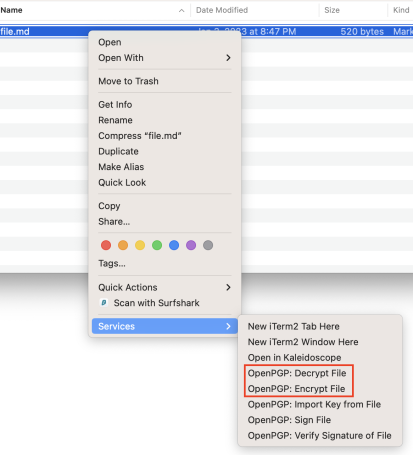
This will generate a new, encrypted file with extension .gpg. You can go ahead and share this file with confidence that the information can only be decrypted by the recipient you chose using their private key.
You are done, you are not sending files that are properly encrypted, and as they say “Dance like nobody is watching and encrypt like everyone is”.

